
Wedge Formation

War Sattelites

IEW to force structure

war strategy

Brigade turning movement

War strategy

war strategy

war strategy

war strategy

war structure

war structure

Platoon Wedge formation

Military deception

VC/NVA attack doctrine

Cyberspace

Pool of Regular Reserve Forces

Army Ranks
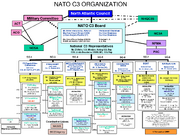
NATO Organization

Doctrine Architecture

European Military

Army structure

NCISS Structure

Army Structure

New NATO Command Structure

German Infantry Division

Phases of Cyberwarfare

Coalition ISR Sensor Environment

Cyber war

Unified Field
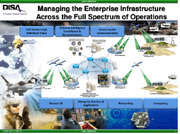
Enterprise Infrastructure

NATO Expansion

Domains of Electromagnetic Spectrum
http://en.wikipedia.org/wiki/Electronic_warfare http://en.wikipedia.org/wiki/Ground_warfare
http://www.army.gov.au/ http://www.firstworldwar.com/index.htm
http://www.history.army.mil/books/AMH-V2/AMH%20V2/index.htm#cont
http://fas.org/spp/military/docops/defense/97_jwstp/jwstp.htm

Ambush and Cavalry
http://en.wikipedia.org/wiki/Armoured_warfare http://www.dtic.mil/doctrine/new_pubs/jp3_0.pdf http://en.wikipedia.org/wiki/Joint_warfare http://www.tanks.net/

Allah Creator
H. ELECTRONIC COMBAT
1. Definition
Electronic Combat (EC) encompasses the capability to disrupt or degrade an enemy's defenses throughout the areas and times—and across the entire electronic, infrared (IR), and visual spectrums—required to permit the deployment and employment of U.S. and allied combat systems. EC (also known as electronic warfare, or EW) includes capabilities for deceiving, disrupting, or destroying enemy surveillance, command and control (C2), and weapon systems/sensors (e.g., early warning, acquisition, and targeting functions) associated with the enemy's integrated air/area defense network. EC also includes the critical capabilities of recognizing attempts by hostile systems to track or engage U.S. or friendly forces, automatically initiating the appropriate countermeasures or defensive response, and protecting friendly systems through redundancy and hardening.
2. Operational Capability Elements
The strategic goal of EC is to control and exploit the electromagnetic spectrum for maximum effectiveness of U.S. military operations—that is, to deny, disrupt, degrade, deceive, or exploit enemy use of the full electromagnetic spectrum while ensuring its use by friendly or joint forces. Successful attainment of this goal necessarily confers a superior capability on U.S. military and friendly forces to survive in their execution of all required combat/conflict operations/missions. EC has three principal and integral operational capability elements: electronic attack, electronic protection, and electronic support. Each element provides a range of benefits to participants in joint organizations and operations. Figure IV.H-1 depicts these principal elements as they contribute to joint operations.
Electronic attack (EA) involves the defensive or offensive protection of U.S. forces and platforms against hostile weapon, sensor, and C3 systems. In its traditional form ("self-protection"), EA consists of a warning receiver to warn of impending weapon attack ("attack warning"), expendable countermeasures, and a jamming system working in concert to prevent sensor-guided weapons from hitting their target. More recent technology further expands the boundaries of electronic attack by engaging sophisticated, long-range target acquisition sensors—such as airborne and space-based surveillance/synthetic aperture radars, and the increasingly modern communications supporting all

Creator of a Billion Light Years Away Ombudsman
phases of the enemy attack or defense—thereby becoming a key, integral element of battlespace dominance. Therefore, EC/EW and its EA element plays a prominent, vital role in the new, "leveraged" concept of Full Dimensional Protection, as described in the Chairman of the Joint Chiefs of Staff's Joint Vision 2010.
One critical aspect of electronic attack is the ability to deny an opponent the reliable use of their own command, control, communications, and computer/intelligence, surveillance, and reconnaissance (C4ISR) systems—thereby permitting U.S. platforms and forces to operate freely throughout the battlespace with minimal loss to hostile weapons. Such freedom is gained due to confusion, analysis, and decision delays induced and propagated within the enemy's C4ISR infrastructure regarding the location(s), structure, and intent of joint forces. This EA strategy is an enabling capability for operations requiring penetration of hostile territory (e.g., suppression of enemy air defenses (SEAD), close air support (CAS), counter-C3, and precision attack on any fixed or mobile target). Thus, again, electronic attack plays a prominent role in the Joint Vision 2010 concept of Dominant Maneuver by virtue of aiding the control of operational tempo, and EA is synergistic with the Joint Warfighting Capability Objective (JWCO) of Information Superiority.
Figure IV.H-1. Concept—Electronic CombatElectronic protection (EP) supports the development of design features and employment techniques that allow U.S. forces to enjoy the benefits of accurate electronic sensors and systems, both offense and defensive—despite an environment that includes hostile jamming, deception activity, and enemy weapon targeting that, itself, depends on detecting, recognizing, and determining the location of U.S. emitters. EP allows operational users to initiate and prosecute a mission without degradation from opposing EW or from conventional or directed-energy weapons cued or targeted by hostile sensors. Successes in EP techniques translate into effective targeting by joint combatants and reliable communications, surveillance, and electronic support sensors—corresponding to the JWCOs of Precision Force and Information Superiority.
Electronic support (ES) is the EC element that gathers, consolidates, and employs information from hostile or potentially hostile electronic sensors and C3 systems. ES is critical to developing a comprehensive picture of the battlespace and a reliable indication of hostile force movement and intentions. ES allows force avoidance, efficient engagement, and electronic deception—EA—of enemy sensors, weapons, and communications systems. The classic definition of electronic support recognizes its functionality from the joint operational commander level down to the "single-seat" cockpit combatant. With increasingly sophisticated, worldwide, modern weapon systems, the pressures for ever-increasing ES fidelity are blurring the older distinctions between the classic radar warning receiver (attack warning) and the longer range electronic support measures (ESM) systems. Therefore, in the future, all joint combatants/platforms can be integrated into the battlespace picture via the contributions of their ES systems. ES enables a wide range of operational options that contribute to virtually every combat and peacekeeping mission. Hence, ES is strongly synergistic with the JWCOs of Precision Force, Combat Identification, and Information Superiority and the associated Joint Vision 2010 concept of Precision Engagement.
3. Functional Capabilities
Table IV.H-1 depicts the relationships between operational capability elements and functional capabilities for the EA and ES components of EC. Because electronic protection capabilities are generally specific to a sensor or C3 system, the EP component is not addressed further in this section.1 From a basic technology perspective, refer to the Defense Technology Area Plan (DTAP), Chapter VII, Sensors, Electronics, and Battlespace Environment; and Chapter X, Weapons (EW Mission Support).
Table IV.H-1. Functional Capabilities Needed—Electronic Combat
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Strong Support | Moderate Support | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||

Strategy TSF

Strategy TSF

Format TSF Mechas
4. Current Capabilities, Deficiencies, and Barriers
Current EC/EW capabilities are generally the result of extensive, detailed concentration on the capabilities of the former Soviet Union; a coherent "successor" threat has not yet been established. However, it is clear that generic trends exist in global military technology that allow identification of the most prominent deficiencies and barriers to joint EW operations. Table IV.H-2 provides a top-level summary of capabilities, limitations, and key technologies to overcome current limitations and to provide those capabilities.
The threat of passively guided weapons has increased dramatically over the past decade. Today, infrared-guided weapons pose a serious and growing threat to U.S. forces and platforms in the air, on land, and at sea. Inexpensive, portable missiles can be launched with ease and effectiveness against all airborne combatants. The threat of longer range infrared guided antiship missiles is equally great, and formidable in both at-sea and littoral scenarios. Land combat vehicles are similarly threatened by frontal and top-attack munitions guided by infrared and multispectral seekers. Protection against infrared guided weapons is the highest priority need in electronic attack and is an important deficiency that constrains the efficient execution of joint operations.
The technology barriers to resolutions of these EA deficiencies include inadequate detection range and angular resolution on attack warning systems to eject decoys or initiate jamming; insufficient power, low efficiency, and unacceptable size, weight, and cost of laser devices that could be used in countermeasure systems; and insufficient output power and excessive size, weight, and cost of high-power microwave systems for self-protection of platforms. Of particular concern in the high-power microwave arena is the integration of this weapons-level EC effect into operational concepts of Joint Forces—so as to avoid/mitigate the possible, self-inflicted, mission-degrading effects of electronics fratricide and platform "suicide." Each of these barriers is being addressed with ongoing technology demonstration programs.
As a second area of high EA priority, the rapid development and adoption of new communications technology has created deficiencies in the ability of U.S. forces to exploit and selectively disrupt modern signals. Cellular and personal communications systems used by civilians and hostile forces, and high-capacity digital, multichannel networks associated with distributed information systems, pose particularly difficult technical challenges. The ability to detect, analyze, exploit, and disrupt these signals is fundamental to the conduct of joint operations against an opponent with modern communications equipment and sensors. In the context of EA, jamming transmitters and antennas used against C3 signals require improvements in precise modulation selection and modulator control, linearity, efficiency, output power, and directivity.
Electronic protection measures are generally specific to a sensor or C3 system. EP measures entail the tailoring of generic protection technology and techniques (again, as treated in the respective DTAP sections) to satisfy the electronic protection requirements of a specific system in order to ameliorate the effects of hostile jamming, deception, targeting, or directed-energy attack. Although included as an element of EC, these efforts are an integral part of the sensor or C3 development program (e.g., GPS). As stated previously and noted at the end of Table IV.H-2, further EP details are omitted from this section.

MDA Missile Defense
Table IV.H-2. Goals, Limitations, and Technologies—Electronic Combat .
| Goal | Functional Capabilities | Limitations | Key Technologies |
|---|---|---|---|
| Operational Capability Element: Electronic Attack—Platform Protection | |||
| >99 percent combined probability of no hostile weapon launches, and/or weapon miss. | Attack Warning
Real-time RF threat detection, ID, and geolocation Missile approach warning Modular, programmable EW receiver/processor Sensor/data fusion, electronic intelligence |
Slow, inaccurate, and ambiguous threat ID and bearing resolution Limited probability of intercept in dense, high signal, high clutter environment Simultaneous, overlapping signals Incomplete/uncorrelated apriori database information Unpredictable emitter mode changes, and tracking thereof |
Advanced signal ID and detection algorithms Distributed/parallel COTS multiprocessors High sensitivity, multiband IR detectors/sensors Directional apertures Digital and channelized receivers Low false alarm, high sensitivity missile warning, with accurate "time to go" Real-time techniques for correlation/fusion of all-source information/data |
| Expendable/Decoy Countermeasures
Decoy terminal threat weapons UAV employment Robust, multispectral EA of simultaneous threats |
Slow, inaccurate, and ambiguous threat ID and bearing resolution Unmatched/incoherent spectral content and output profile/signatures Tight packaging constraints High cost of integrating multispectral capability(s) Inaccurate ejection timing, leading to rapid stores depletion Unacceptably high false alarm rate |
Advanced signal ID and detection algorithms High sensitivity, multiband detectors Digital and channelized receivers Low false alarm, high sensitivity missile warning, with accurate "time to go" Enhanced IR flare materials Kinematic/aerodynamic techniques Digital RF memories (DRFMs) VHSIC/application specific ICs (ASICs) MMIC/microwave power module (MPM) amplifier technologies Cooperative DIRCM/laser-based IRCM EA techniques Signature modification/control and location masking techniques (e.g., chaff, smoke, aerosols) | |
| Coherent Jamming
Robust, multispectral EA of simultaneous threats Broadband, coherent, surgical RFCM Second-generation directed IRCM (DIRCM) Laser-based IRCM Counter IADS surveillance, acquisition, and C2 |
Slow, inaccurate, and ambiguous threat ID and bearing resolution Limited probability of intercept in dense, high signal, high clutter environment Simultaneous, overlapping signals Unpredictable emitter mode changes, and tracking thereof Unmatched/incoherent spectral content and output profile/signatures Tight packaging constraints High cost of integrating multispectral capability(s) High retrofit costs Nonintegrated approach to EA of multispectral/multimode threats |
Advanced signal ID and detection algorithms High sensitivity, multiband detectors Directional apertures Digital and channelized receivers Digital RF memories (DRFMs) VHSIC/application specific ICs (ASICs) MMIC/microwave power module (MPM) amplifier technologies Cooperative DIRCM/laser-based IRCM EA techniques Signature modification/control and location masking techniques (e.g., chaff, smoke, aerosols) Affordable, compact laser (minimum 2W/20kHz, mid IR) Coherent, doppler, monopulse, and false target CM techniques | |
| Operational Capability Element: Electronic Attack—C2W and SEAD | |||
| Exploit, disrupt, deceive modern integrated defense system/network | Complex C2 Signal Identification
Real-time RF threat detection, ID, and geolocation Modular, programmable EW receiver/processor Sensor/data fusion, electronic intelligence UAV employment |
Slow, inaccurate, and ambiguous threat ID and bearing resolution Limited probability of intercept in dense, high signal, high clutter environment Simultaneous, overlapping signals Unpredictable emitter mode changes, and tracking thereof Tight packaging constraints High retrofit costs Insufficient low-noise signal intercept and decoding techniques Inability to track/jam in real time |
Advanced signal ID and detection algorithms Distributed/parallel COTS multiprocessors Directional apertures Digital and channelized receivers Real-time techniques for correlation/fusion of all-source information/data VHSIC/application specific ICs (ASICs) Negative signal-to-noise (SNR) signal and code ID/tracking algorithms Parallel signal channel tracking and algorithm techniques Near-real-time code breaking techniques |
| Nonfratricidal C2 Jamming
UAV employment Broadband, coherent, surgical RFCM Counter IADS surveillance, acquisition, and C2 |
Slow, inaccurate, and ambiguous threat ID and bearing resolution Limited probability of intercept in dense, high signal, high clutter environment Simultaneous, overlapping signals Unpredictable emitter mode changes, and tracking thereof Tight packaging constraints High retrofit costs Inability to track/jam in real time Nonlinear power amplification Imprecise coding/signal demodulation Poor beam/radiation control |
Distributed/parallel COTS multiprocessors Digital and channelized receivers Digital RF memories (DRFMs) VHSIC/application specific ICs (ASICs) Negative signal-to-noise (SNR) signal and code ID/tracking algorithms Near-real-time code breaking techniques High efficiency, linear, solid-state amplifiers (HF, VHF, UHF) C2 frequency MPMs Efficient HF, VHF, UHF antenna designs (e.g., high temperature superconductivity, arrays) | |
| Lethal SEAD
Real-time RF threat detection, ID, and geolocation Modular, programmable EW receiver/processor Sensor/data fusion, electronic intelligence Decoy terminal threat weapons UAV employment Robust, multispectral EA of simultaneous threats Broadband, coherent, surgical RFCM Counter IADS surveillance, acquisition, and C2 |
Slow, inaccurate, and ambiguous threat ID and bearing resolution Simultaneous, overlapping signals Incomplete/uncorrelated apriori database information Unpredictable emitter mode changes, and tracking thereof Unmatched/incoherent spectral content and output profile/signatures Tight packaging constraints High cost of integrating multispectral capability(s) Affordability of UAV decoys Affordable, compact RF support jamming (stand-off/stand-in techniques) |
Advanced signal ID and detection algorithms Distributed/parallel COTS multiprocessors Directional apertures Digital and channelized receivers Digital RF memories (DRFMs) VHSIC/application specific ICs (ASICs) MMIC/microwave power module (MPM) amplifier technologies Frequency/bandwidth aperture function control techniques (EA vs. ES) Large-extent phased arrays | |
| Operational Capability Element: Electronic Support | |||
| > 99 percent probability of signal intercept, detection, ID, and location across EM spectrum, mission, and battlespace. | High Fidelity Signal Recognition and Tracking
Real-time RF threat detection, ID, and geolocation Missile approach warning
|
Slow, inaccurate, and ambiguous threat ID and bearing resolution Limited probability of intercept in dense, high signal, high clutter environment Simultaneous, overlapping signals Incomplete/uncorrelated apriori database information Unpredictable emitter mode changes, and tracking thereof High retrofit costs Insufficient low-noise signal intercept and decoding techniques Insufficient processing time and "power" Little interoperability between operational/service systems |
Advanced signal ID and detection algorithms Distributed/parallel COTS multiprocessors High sensitivity, multiband detectors Directional apertures Digital and channelized receivers Low false alarm, high sensitivity missile warning, with accurate "time to go" Real-time techniques for correlation/fusion of all-source information/data VHSIC/application specific ICs (ASICs) Negative signal-to-noise (SNR) signal and code ID/tracking algorithms Parallel signal channel tracking and algorithm techniques Near-real-time code breaking techniques Sub 1° DF aperture/beamforming systems Rapid (e.g., GHz), high fidelity (e.g., 10-14 bit) analog-to-digital conversion (ADC) hardware/processing Software-reconfigurable/"open" architectures |
| All-Source Data Integration/Fusion
Sensor/data fusion, electronic intelligence |
Slow, inaccurate, and ambiguous threat ID and bearing resolution Limited probability of intercept in dense, high signal, high clutter environment Simultaneous, overlapping signals Incomplete/uncorrelated apriori database information Unpredictable emitter mode changes, and tracking thereof Imprecise coding/signal demodulation Insufficient processing time and "power" Inability to deal with missing, incomplete, and corrupted data |
Advanced signal ID and detection algorithms Distributed/parallel COTS multiprocessors Directional apertures Digital and channelized receivers Real-time techniques for correlation/fusion of all-source information/data Software-reconfigurable/"open" architectures Expert systems and algorithms (knowledge-based information representation and computer "reasoning" techniques that allow manipulation of sensor, text, and archival/library data in one process) | |
| Hostile Battlespace Signal Intercept/Collection
UAV employment Counter IADS surveillance, acquisition, and C2 |
Vulnerability of conventional manned platforms |
Advanced signal ID and detection algorithms Distributed/parallel COTS multiprocessors Digital and channelized receivers Real-time techniques for correlation/fusion of all-source information/data VHSIC/application specific ICs (ASICs) Near-real-time code breaking techniques Rapid (e.g., GHz), high fidelity (e.g., 10-14 bit) analog-to-digital conversion (ADC) hardware/processing Software-reconfigurable/"open" architectures UAV payloads Wideband datalinking | |
| |||
| Operational Capability Element: Electronic Protection | |||
| Not considered in this document | |||
Electronic support is the activity that gathers timely information on hostile force composition, status, and intentions by intercepting and analyzing the signals from hostile electronic systems and integrating this information with that from our own forces and electronic systems—whether at the joint command, at-sea battlegroup, or single-seat cockpit/battlefield soldier level. The composition and characteristics of C3 systems are changing rapidly as low-cost, high-performance digital technology becomes universally available. The proliferation of this technology has also encouraged the widespread availability of cellular and personal communications devices that are highly mobile and resistant to conventional electronic attacks. Optical fiber networks, coupled with increasingly more powerful computers, constitute the basis for powerful information systems that support sophisticated military C3 functions as easily as civilian applications. These advances in processing and communications technology facilitate and encourage the acquisition of customized, unique C3 systems in the military forces of many small countries. This diversity and unpredictability constitutes a formidable challenge to ES organizations that must support operational users with services and products in any conceivable location and situation.
As advanced knowledge of threat system parameters—necessary for attack warning and countermeasure waveform development—becomes more difficult to obtain, EW receivers on tactical aircraft, ships, and land combatants will have to assume some of the burden formerly assigned to dedicated special signal collection receivers (i.e., the "blurring" regarding ES as discussed in Subsection 2, above). This will be necessary to accumulate detailed information on classes of emitters, as well as individual emitters, and to support the development of generic system recognition algorithms.
The ability to fuse different forms of information from multiple sources is an important capability in an environment of mixed-media signals. Algorithms that can analyze and consolidate information from different sensors and databases can produce a product that is more complete and informative than the sequential examination of the individual contributions. Algorithms using expert system techniques and artificial intelligence principles can represent and manipulate knowledge faster and more exhaustively than is possible with human analysts in time-critical situations.
The technology deficiencies in electronic combat include incomplete development of technologies suitable for unmanned aerial vehicles (UAVs) for signal collection/ES missions (and linkages/extrapolations of this technology to broadband RF support EA countermeasures from UAV platforms); inadequate processing subsystems and algorithms for detection, identification, and analysis of new communications waveforms; unacceptable performance in signal collection against mixed-media networks containing fiber optic and other transmission media; and inadequate performance and excessive cost to acquire and maintain warning and signal collection capabilities in tactical EW receivers. Finally, current capabilities in the representation of data, automated sensor product analyses, and machine reasoning capabilities are insufficient to perform timely and complete sensor product and data fusion.
Figure IV.H-2 illustrates how technology developments support technical demonstrations that contribute to operational capability elements in Electronic Combat. Table IV.H-3 lists planned DTOs for EC, the details of which can be found in the DTO volume for the JWSTP and the DTAP. Table IV.H-4 correlates the technical demonstrations with the operational capability elements they support.
5. Technology Plan
As emphasized above, a critical, coordinated tri-service plan to address vulnerability to IR missiles and weapons has been developed under Defense Reliance and is being executed. The program includes near to mid term measures to reduce vulnerabilities by using improved missile warning capabilities and advanced flares. Coupled with laser source work under the DTAP (DARPA and WE.43.08), conventional laser-based infrared countermeasures (IRCM) solutions are in progress—notably the current work under DTOs H.02 (for rotary-wing aircraft) and H.05 (for large aircraft). Additionally, an ATD is scheduled to conclude this fiscal year that will establish baseline data on future open-loop, laser-based IRCM architectures for planned Reliance collaboration in the tactical aircraft arena (TACAIR DIRCM). With regard to surface ship combatants, 1996 plans to pursue a laser-based IRCM ACTD for the large-ship class have been superseded by the inclusion of the technology (from its successful 1994-95 ATD) into 6.4 development work in conjunction with the Advanced Integrated EW System (AIEWS).
Capabilities to attack hostile command and control (C2) networks will vastly improve with the development of transmitters with more efficient power amplification; modern, digital, EA modulation formats; and greater angular precision. These enhancements will effectively increase jamming power on victim systems and reduce interference with U.S. and allied systems in the vicinity. A coordinated tri-service effort will develop signal separation, recognition, analysis, and countermeasure techniques against specific waveforms used in C2 applications. These ES capabilities will be consolidated with the jamming improvements developed as an electronic attack measure to produce an improved ability to selectively disrupt hostile communications and weapon control networks.
Figure IV.H-2. Technology to Capability—Electronic Combat Table IV.H-3. Defense Technology Objectives—Electronic Combat
| DTO No. | Title |
|---|---|
| H.02 | Multispectral Countermeasures ATD |
| H.04 | Miniature Air-Launched Decoy ACTD |
| H.05 | Large Aircraft Infrared Countermeasures (IRCM) ATD |
| H.06 | Advanced Electronic Countermeasures Transmitter ATD |
| H.07 | Enhanced Situation Awareness Insertion ATD |
| H.08 | Onboard Electronic Countermeasures Upgrade ATD |
| H.09 | Sensor Fusion/Integrated Situation Assessment Technology Demonstrations |
| A.04 | Information Operations C2 |
| WE.03.08 (past) | Combat Aircraft IRCM (TACAIR DIRCM ATD portion thereof) |
| WE.09.08 (past) | DARPA/Tri-Service IRCM Laser Technology |
| WE.19.08 | High-Power Microwave Aircraft Self-Protect Missile Countermeasures |
| WE.23.08 | Modern Network Command and Control Warfare Technology |
| WE.40.08 | Infrared Decoy Technology |
| WE.42.08 | Laser Aircraft Self-Protect Missile Countermeasures |
| WE.43.08 | Advanced Multiband Infrared Countermeasures Laser Source Solution Technology |
| WE.46.08 | Coherent Radio Frequency Countermeasures Technology |
| WE.47.08 | Imaging Infrared Seeker Countermeasures Technology |
| WE.48.08 | Missile Warning Sensor Technology |
Similarly, a coordinated development is under way to design and integrate critical digital receiver/processor technologies to yield next-generation EW receivers and receiver upgrades. These receivers will be capable of performing warning, signal parameter collection, and situation assessment; and assisting the functions of threat geolocation and combat ID. Associated architectures will integrate the advantages of broadband, channelized monolithic receivers "on a chip" with commercial, real-time, parallel digital signal processors to yield an affordable, adaptable, software-reconfigurable capability. A concurrent affordability thrust is planned by the Navy in FY97-98 to "productize" the 6.2-developed monolithic microwave integrated circuit (MMIC) receiver-channelizer, with firm expectations to achieve hundredfold reductions in cost, size, weight, and increased reliability. In conjunction with DARPA/AF work on advanced digital receiver components/interconnects, these capabilities will serve to fill a number of future operational deficiencies that are now represented by more than a dozen individual systems.
The major push in the Suppression of Enemy Air Defense (SEAD) area is the Miniature Air-Launched Decoy (MALD) ACTD Program (H.04). To augment the EW "triad" of the future (standoff communications jamming, SEAD, and standoff radar jamming), a joint development effort is being planned to design and develop the next-generation support jammer. Key to the program is the adoption of a reconfigurable pod/UAV concept that will not depend on a dedicated airframe in the future. Synergies of the technologies involved will also have joint applications to affordable upgrades to jamming systems of all three services and their respective platforms (DTAP DTO WE.46.08, Coherent RF Countermeasures Technology, and H.06/ H.08).
Table IV.H-4. Demonstration Support—Electronic Combat
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Strong Support | Moderate Support | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Figure IV.H-3 is a roadmap for developing and demonstrating the technologies required to support the operational advances in Electronic Combat. This roadmap concentrates on the themes of IRCM (air, land, and sea platforms); offensive C2 Warfare/Information Warfare; precision emitter location and battlespace SA; upgrades to our aging joint combatant platforms; and the valuable "force multiplier" aspects of support jamming.
6. Summary
Figure IV.H-4 shows how this investment strategy will provide incremental improvements to Electronic Combat. This section on the Electronic Combat JWCO describes a well-balanced approach to achieve platform protection and electronic support to all joint combatants. The plan emphasizes solutions to the formidable, worldwide IR missile threats; multispectral situation awareness; countering the C2 hierarchies of the hostile force while preserving real-time knowledge of the enemy; and countering the enemy early in the engagement process via the EC triad of C2 Warfare, SEAD, and RF support jamming.
Armoured warfare was to dominate the German attack on Western Europe in May 1940. Holland fell to the use of paratroopers, but it was armoured vehicles used in blitzkrieg attacks that were to be crucial in this phase in World War Two.
|
Guderian - the father of blitzkrieg |
On August 8th 1918, 430 British tanks had attacked German lines on the Western Front. In one day, British forces advanced five miles into German lines. Such an attack convinced Luderdorff that Germany would not be able to stand up against another armoured attack and by November 1918 an armistice had been signed. The shock that accompanied this attack was overwhelming. Ironically, the attack on the 8th August was nowhere near as devastating as Luderndorff believed as the British tanks had advanced much further than their supply lines could cope with and even though they had penetrated five miles, they had not got much further than the forward German defences. However, their psychological impact had been huge. This is what had caught the eye of German officers such as General von Kuhl, who had been on the receiving end of the August attack. In 1928, Kuhl wrote with huge enthusiasm about the impact of tanks and the surprise factor they gave to commanders in the field.
Neither France nor Britain shared Kuhl’s enthusiasm for the tank. In the inter-war years, France put her faith in the defensive – hence the building of the Maginot Line. Such a strategy – the so-called ‘continuous line’ – meant that the tank was never seen as anything more than a vehicle that could support the infantry wherever it was needed. The other role given to it was one of reconnaissance. However, the tank was not a weapon considered good enough to drive a gaping hole through the enemy and inflicting major damage to it. In Britain, the military hierarchy was still dominated by the old established cavalry or Guards regiments. The tank did not fit into their way of thinking as the cavalry still had a love affair with the use of the horse in battle while the Guards regiments were all infantry based. Also, those who did not support the tank also pointed out that despite the achievements of the tank in August 1918, many had been lost in battle or had broken down, thus questioning their reliability in battle. To some in the inter-war years, the cost of tanks was an issue. Horses were cheaper, some saw them as more reliable and there was also a comfort zone with them.
After the success of blitzkrieg in September 1939 against Poland, the French tinkered with their strategy involving tanks. Each of the four light mechanised divisions the French had by May 1940, had 220 tanks and armoured cars in them. Combined with a brigade of infantry, this was a formidable force on paper. However, the importance of defence still prevailed and the tank was seen even in May 1940 as a means of supporting infantry as opposed to a weapon in its own right. The French had also created at the last minute four heavy mechanised divisions with heavy tanks and fewer infantry. But even these heavy tanks were seen as just being able to punch a hole through the German line through which the infantry could move through – once again tying the tanks to the infantry.
In Germany, the Wehrmacht had to effectively start from scratch after the Treaty of Versailles imposed its military terms on Germany. With just 100,000 men allowed, German senior commanders needed to find ways and means to bolster the fighting capacity of the army. This does not mean that all German senior commanders were supporters of the tank. Luderndorff, though no longer in the military, had not been a supporter of the tank and some of the old guard in the army carried on this belief. However, a new generation of young officers embraced the idea of a fast moving war based on armoured vehicles supported by air power. After Hitler came to power in January 1933, he gave these officers his backing against the more conservative views of the old guard. As a man who had experienced the horrors of trench warfare, it is possible that Hitler, even though he planned wars of conquest, was keen to ensure that trench warfare never occurred again. Men such as Guderian and Rommel were given a free hand to develop tactics based on mobility, while tank designers were also given encouragement from the highest level.
In September 1939, when blitzkrieg was unleashed on Poland, many senior German military commanders were not convinced it would work. They were proved wrong. Even in the build up to the May 1940 attack, senior figures such as Brauchitsch and Halder, supported by Bock, Leeb and Rundstedt, tried to persuade Hitler against a mass armoured attack on the French. Once again, blitzkrieg worked and only served to advance in Hitler’s mind the standing of advanced thinkers such as Guderian and Rommel (and his own military ‘genius’) – and undermine the standing of men such as Brauchitsch.
Ironically, not all of the British Army was devoid of forward thinkers. Three of the main people associated with what was known as the “Tank Idea” were Captain Liddell Hart and Generals Percy Hobart and J F C Fuller. In particular, Hobart was driven by the idea of creating a fighting force based on the mobility of tanks that could drive through an enemy’s line. He envisaged mobile infantry and artillery units to support the tanks. However, he came up against the entrenched views of the establishment in the military and despite being commander of the 1st Tank Brigade, he had little chance against the traditionalists. These traditionalists found support in political circles as well. In 1934, the Financial Secretary to the War Office was Duff Cooper. He stated in that year:
| “The more I study them (military affairs) the more I become impressed by the importance of (horsed) cavalry in modern warfare.” |
Ominously for the likes of Hobart and Fuller, Duff Copper became Secretary of State for War in 1935.
It was only in 1937, that Britain decided to invest in tanks en masse. However, by May 1940, very few of the new tank units had any form of experience in operating with infantry units – and certainly not in a war situation.
In May 1940, the BEF had seven cavalry light armoured regiments mounted in light tanks and their task was one of reconnaissance and supporting the infantry – just as cavalry units had done. Neither the French nor the British had devised a plan on what to do against a major German armoured thrust. They had designated certain areas along the frontier as “tank proof”, areas where tanks and other vehicles could not operate due to the terrain. The Ardennes was one of these places – exactly the area where the Germans were to launch a massive armoured attack on Sedan and then drive through to Abbeville.
Many assume that the success of the May 1940 attack on the west is indicative of the superiority of Germany’s tanks when compared to the British and French ones. This is misleading. The Panzer III and IV’s were well armed but poorly armoured when compared to British and French tanks. But Germany only had 627 of these tanks. The armour of these tanks was no more than 30 mm which gave both Marks little armour against a direct hit. The other ‘tanks’ available to the Wehrmacht at this time were no more than lightly armoured vehicles – good for speed and reconnaissance but of little value in a one-to-one with a French/British tank.
The French Char B was a fine tank – well armed and well armoured. It had a 47-mm gun in a fully rotating turret and a 75-mm gun in the hull. Its armour ranged from 40-mm to 60-mm. The French had 800 of these tanks. But they had one major failing. The commander in the turret had to command the vehicle, load and fire the gun and invariably take some part in the tactics being used on a local level. Such a responsibility meant that he could not concentrate on one thing. The German III and IV’s had three men sharing these duties, as did the British.
British tanks did include many light armoured vehicles that would not really pass as tanks. But in the Matilda they had a fine tank with armour of up to 70-mm and a two-pounder gun. No German tank shell could penetrate the Matilda’s hull and few German tanks could match the firepower of the two-pounder.
So why were the German so successful when it came to the actual attack on May 10th when so much of the Allies equipment was as good as the Germans or better? The answer must always go back to the tactics employed. Once the Germans had attacked into the Ardennes, they gained a momentum, combined with air superiority, that the Allies could not handle. As tanks were used to support the infantry, the Allies found that they had no answer to the constant onslaught of blitzkrieg, despite having tanks as good or better than the Germans. The overwhelming success of blitzkrieg pushed the Allies back to the beaches around Dunkirk which required Operation Dynamo to rescue British and French troops who had to leave all their vehicles behind.
Maneuver leaders must understand operational art, joint operations, and multinational operations because wars are won—with the close cooperation of joint services and multinational allies—at the operational and strategic levels. A string of tactical victories does not guarantee success at the operational or strategic level. As a result, maneuver leaders at all levels must understand the strategic and operational context of their tactical operations.
At the same time, maneuver leaders must also understand the capabilities of joint and interagency partners, and our allies. To seize, retain, and exploit the initiative against a wide array of adaptive and determined enemies, maneuver leaders must effectively employ a potent combination of joint and multi-national assets as part of a combined arms, air-ground team. And just as understanding the strategic and operational context of tactical operations is an important first step in applying the “operational art,” understanding the capabilities, limitations, organizations, and interests of our joint and multi-national partners will be critical to maneuver leaders as they seek to assist friends, reassure and protect populations, and identify, isolate, and defeat enemies.
Operational Art, Joint Operations, and Multinational Operations[]
“In forming the plan of a campaign, it is requisite to foresee everything the enemy may do, and be prepared with the necessary means to counteract it. Plans of the campaign may be modified ad infintium according to the circumstances, the genius of the general, the character of the troops, and the features of the country.” Napoleon “The only thing worse than fighting with allies is fighting without them.” Winston Churchill
In today’s wars and in future armed conflict, maneuver leaders will face a wide array of complex challenges. The continuing proliferation (and even use) of weapons of mass destruction, steadily worsening economic conditions, social disorder throughout the world, an increasing rise in militant extremism (both religious and political), the growth of terrorist activities and operations, and a growing number of technically sophisticated hybrid threats and regionally-focused conventional armies are just a small sample of the potential and real dangers our maneuver forces will face.
As a result, US Army maneuver forces must be capable of defeating conventional forces, well-equipped hybrid surrogates, and indigenous paramilitary forces, insurgents, and terrorists. We must be capable of operating in jungles, mountains, deserts, and cities. Moreover, we must be prepared to operate with our fellow services and in the company of our allies and indigenous forces. And throughout all these complexities, the maneuver leader must have the vision and context to understand how best to array the tactical combat power allocated to him in a manner that will ultimately achieve the national policy aims of the United States. In other words, maneuver leaders must understand how to employ the operational art in the context of joint and multinational operations.
Operational Art[]
According to Joint Publication 3-0, Joint Operations, operational art is “the cognitive approach by commanders and staffs—supported by their skill, knowledge, experience, creativity, and judgment—to develop strategies, campaigns, and operations to organize and employ military forces by integrating ends, ways, and means.” In other words, operational art is the employment of military forces to attain strategic goals through the design, organization, and conduct of campaigns and major operations. If strategy attempts to align military, diplomatic, informational, and economic resources to meet national policy goals and tactics attempts to employ small units (squad to Brigade) on the battlefield, then operational art is the means through which commanders connect tactical combat power to the achievement of national policy objectives.
Highly contextualized and endlessly variable, operational art requires broad vision; a clear understanding of the operational environment, strategic goals, and tactical capabilities; the ability to anticipate future events; a nuanced understanding of the relationship of means to ends; clear communication to articulate a sequence of complex events; and effective joint and multinational cooperation. At its essence, operational art demands that maneuver leaders understand the following first-order questions:
- What is the necessary military and political condition required to achieve the strategic goal?
- What sequence of tactical and operational actions are most likely to produce that condition?
- How should the operational commander apply tactical resources to accomplish that sequence of actions?
Joint Operations and Multinational Operations[]
Maneuver leaders must understand the role of operational art in the context of joint and multinational operations. According to Joint Publication 1-0, Doctrine for the Armed Forces of the United States, joint operations consist of military “activities, operations, and organizations in which elements of two or more Military Departments participate.” For example, the assault into Iraq and the subsequent attack to Baghdad in March 2003 was a joint operation. Ground forces from the US Army fought in concert with the US Marine Corps while both the Marines and the Army were supported by combat aircraft from the US Air Force and the US Navy. Likewise, multinational operations, as defined by Joint Publication 3-16, Multinational Operations, are military “operations conducted by forces of two or more nations.” Multinational operations can result in the formation of coalitions—where an ad hoc arrangement between two or more nations forms a consensus for common action—or in the result of alliances—where a formal agreement (usually a treaty) between two or more nations establishes broad, long-term objectives that further the common interests of the members. For example, the Anglo-Canadian-American assault on Nazi-occupied France in June 1944 was a multinational operation.
Significantly, maneuver leaders must understand the potential opportunities, synergy, and power of joint and multinational operations. In simple terms, the integrated employment of close-air support, naval power, and land power can generate consider combat power and, when employed through the effective application of the operational art, potentially decisive strategic effects. At the same time, however, maneuver leaders must also understand the difficulties and challenges associated with both joint and multinational operations. For example, communications, logistics, and command functions can present significant compatibility challenges to the commander and subordinates within a joint and multinational force.
Section III: GROUND FORCES
4. GENERAL
Basically, tactics of the Japanese are no different from those employed by other modern armies. In jungle warfare, however, their tactics have been characterized by speed, deception, and the use of modern automatic weapons. In instances when numbers would gain a quick decision, Japanese commanders have not hesitated to commit sufficient force to overwhelm the opposition even though at great cost in Japanese lives.
Thorough reconnaissance usually precedes all operations. Means of communication, particularly radio, are employed even to the lowest units. Camouflage is stressed to include measures taken by the individual soldier. Ruses and feints are extensively employed. The Japanese have quickly discovered that in many instances bluff is far more economical than force.
Lightly dressed and equipped, the Japanese soldier possesses great mobility; generally he is independent of supply lines, and is taught to live off the land.
5. MOVEMENT
The Japanese employ all available means of transportation to move troops speedily along highways and railways, and through jungles and water areas, never failing to utilize civilian, army, and naval conveyances as they are captured. The speed of their movements has been facilitated by light equipment, simple rations, and a minimum amount of clothing, weapons, and ammunition, plus, in many cases, the aid of Fifth Column guides.
a. By Water Craft
The Japanese look on water as a highway, not as an obstacle. In both Malaya and Burma, the Japanese employed small specially-designed river boats and small confiscated civilian boats to infiltrate patrols to the flanks and rear of defending forces. The patrols, sometimes composed of large numbers of troops, generally moved at night. When they moved in daylight, air protection was afforded them. Such movements were possible very often because of the large number of rivers and inlets in Malaya, particularly along the west coast. A succession of infiltrations by boats down the west coast aided greatly in forcing several British withdrawals. The boats usually hid in numerous well-covered inlets by day and traveled close to the coast line at night until reaching their destination. In some cases the Japanese used rafts made of bamboo poles.
b. By Motor
Most of the trucks used by the Japanese to date have been light because of the soggy or rough terrain encountered in nearly all theaters of operation. The trucks have been employed mainly to transport troops and supplies. They usually have been bunched while moving and at a halt, and lights have been used rather freely. Both bunching and lighting afforded excellent targets for the opposition.
c. By Rail
Large quantities of heavy Japanese supplies and some troops were moved by rail from Indo-China and Thailand into northern Malaya. To facilitate repair of railroads and bridges, apparently large stocks of railroad materiel were accumulated in Indo-China before the invasion of Malaya. Japanese engineers appear capable of making quick temporary repairs to damaged railroad and highway bridges.
d. By Air
The Japanese have used air transports for both personnel and supplies, but the extent of such activities is not known. They used 100 transports in a parachute attack on Palembang, Sumatra, and, according to reports, 1,500 troops were transported by air, apparently from Bangkok, possibly from Hanoi, to the vicinity of Chieng-mai in Thailand. It is believed that the enemy uses transport aircraft for aviation supplies, although no detailed intelligence has been received to this effect. It is definitely known that air-borne troops have been trained and that the Japanese began a study of the possibilities of air transport some time before war began.
e. By Bicycles
The Japanese utilized a large number of locally obtained bicycles in Malaya to move troops and light equipment to the front. Usually the riders traveled along the road in single file. Mortars, mortar ammunition, and small arms ammunition were carried on an iron-wheeled vehicle which was attached by a chain to a tandem bicycle propelled by three men.
6. TACTICS
a. Offensive (1) Approach march.—The Japanese company uses roads as far as possible until contact with the enemy is made. One squad1 of each platoon usually travels along the sides of the road and the other squads travel under any available cover on each flank. The leading element of the company consists of 6 scouts, who range about 350 yards ahead of No. 2 platoon (fig. 1). Back of this platoon by 200 to 350 yards is company headquarters, followed closely by No. 3 platoon and then No. 1 platoon. When the squad uses scouts to locate hostile positions, the scouts return to the squad before the attack.
(2) Infiltration.—Once having made contact with the opposition, the Japanese avoid frontal attacks in force and send patrols around the flanks and to the rear of their opposition. These patrols usually are small, consisting of from two to a few dozen men. They are dressed lightly but are armed with light machine guns. Each man carries enough concentrated food to keep him going for several days. These men apparently have been trained thoroughly, hardened for jungle warfare, and given wide discretion as to tactics. They are expert swimmers and boatmen and are otherwise qualified to overcome the difficulties of jungle warfare. They have been instructed to look upon woods and water as means, not obstacles. In the initial stages of the infiltration attacks, small patrols creep noiselessly around the flanks or between defense points to surround the opposition. Usually they remain quiet until their comrades in front of the defenders feint a heavy frontal attack. Then the infiltration patrols open automatic fire to give opposing forces the impression that they have been surrounded. The patrols keep moving about while firing and even when fired on. The volume of fire produced by an unusually large number of automatic weapons in the hands of the patrols and front-line troops indicates stronger forces than those actually engaged. Sometimes the Japanese have set off firecrackers and have made other noises to imitate fire. Sometimes great batches of firecrackers are dropped from planes, with a lighted fuze to ignite them after they fall.
The Japanese seek by these tactics to confuse the defenders; to force quick withdrawals with the hopes of capturing large quantities of weapons, transport, supplies, and men; and to destroy command posts. To aid in accomplishing these aims, some of the patrols are assigned specifically to block roads to the rear.
| Figure 1. Approach march of Japanese infantry company. |
During the Malayan campaign, such infiltration tactics were a constant menace to British artillery, particularly columns on roads. Japanese parties infiltrated between the elements of the columns and prevented them from advancing or retreating. Artillery communication wire in forward zones was cut by the Japanese or native partisans almost as soon as it was laid. After cutting the wire, the enemy troops often hid nearby and fired on the line guards when they approached.
In their infiltration tactics, the Japanese move rapidly at times, and very slowly and patiently on other occasions. They have stood in ditches in rice fields for hours, up to their necks in water, waiting for targets to appear; they have lain concealed in underbrush for long periods waiting for chances to advance without being observed.
In cases of counterattacks, the Japanese permit the opposing forces to pass through, then turn and fire on the flanks and rear of the counterattacking troops.
In both Malaya and the Philippines, some of the infiltrating Japanese, excellently camouflaged, climbed trees, and acted as snipers. They tied themselves to the trees with ropes. Light machine guns carried by the snipers appeared to be fitted with spikes or similar means of rapidly attaching the weapons to trees. The snipers sought particularly to pick off occupants of Bren gun carriers and officers. Occasionally the snipers threw hand grenades into passing trucks and carriers. Trees were used also as observation posts, and on occasions whole parties thus concealed themselves in clumps of woods and dense jungle growth for several days at a time.
(3) Attack.—The Japanese usually begin large-scale attacks at dawn, with the infantry very closely supported by aircraft and artillery.
Their basic principle of attack is to dispose a small force against organized localities and then envelop the flanks and attack the rear. This method has been particularly effective against troops who have been established in an organized position with supplies of food and ammunition at a distance to the rear. The Japanese attack against the flanks and rear of such a position has forced units to withdraw and, occasionally, to fight their way back to regain connection with their ammunition and food supplies. Great speed has characterized the development of such flanking movements which have at times struck 4 or 5 miles in rear of the front line.
(4) Infantry platoon2 tactics.—Squads 1 and 2 of the platoon make frontal assaults while Squad 3 attacks either the opposition's right or left flank (fig. 2). Because of the danger of hitting friendly troops and also of weakening squad strength, the squad rarely ever is divided to attack both flanks at the same time. Squad 4 usually operates fairly close to the front line, in a reserve fire-power position about midway between Squads 1 and 2. The light machine guns of the first three squads generally are used in the front lines—rarely ever as reserve fire power.
The following modification (fig. 3) of the formation shown in figure 2 is sometimes used.
| Figure 2. Usual formation of Japanese platoon for enveloping action. |
| Figure 3. Another formation of Japanese platoon for enveloping action. |
The light machine guns of Squads 1 and 3 support Squad 2 and pin the enemy down with light machine-gun fire. The three grenade dischargers in Squad 4 assist the fixing action with a barrage. The two flank squads (1 and 3) envelop. The envelopment may be of both flanks or of only one flank, in which case the squad not making the envelopment assists Squad 2.
The following quotation from a report indicates a typical Japanese action:
In one instance the Japanese pushed forward in approach formation. On encountering our outposts, they deployed, and at once began to find holes through which they filtered without hesitation, and, after penetrating the outpost line, went around our main body, later firing on it from the rear. The hostile main body apparently lost contact with the connecting files, for they marched directly into a machine gun, which they probably knew of, but thought had been put out of action.
(5) Artillery.—The Japanese have employed relatively little artillery, because of the jungle nature of most of the terrain over which they have fought. They used heavy artillery frequently in the Philippines, principally 240-mm. railway or siege guns, on the United States forts at the entrance of Manila Bay. Upon reaching open country in Johore State, opposite Singapore Island in Malaya, the Japanese began utilizing considerable artillery, a large part of which had been captured. In other than these instances, they have employed small pieces suitable for quick movement through the jungles with infantry. The denseness of jungle growth made use of high trajectory weapons the logical means of obtaining heavy weapon concentration. Under these conditions, they resorted to 81-mm. mortars and occasionally heavy machine guns as substitutes for artillery. Whenever they did use artillery in the jungles, the Japanese made extensive reconnaissance to find the best gun positions available. They put down portable ramps to bridge ditches and soft ground and built gun platforms where it was necessary to fire from soft ground.
(6) Engineers.—Japanese engineers have shown considerable ability and ingenuity in bridging streams and repairing damaged bridges. They have utilized local material whenever possible. It has been reported that in some instances soldiers standing in streams have been used as bridge supports.
b. Armored Forces
(1) General.—So far, the Japanese have used armored forces against the United Nations in small numbers compared with the total number of troops engaged. Jungle growths and restricted terrain have no doubt been the reason, rather than lack of equipment.
Although the exact strength of the Japanese armored units is not known, reports indicate that a year ago there were four tank regiments and a large number of smaller units. Light, medium, and heavy tanks as well as one- and two-man tankettes are in use.
(2) Organization.—Light tanks are an integral part of streamlined divisions. Medium tanks are in nondivisional organizations as are the heavy tanks.3 Tank units are knit together not only by systematic organization but also by providing two-way radios to all tank commanders down to and including platoon leaders.
(a) Divisional.—Most of Japan's "streamlined" divisions have an organic light tank company. The company consists of a headquarters, a rear echelon, and four platoons of three tanks each. Three additional tanks comprise the headquarters and rear echelon. In addition, the rear echelon is believed to have half- track vehicles, motorcycles, and tracked trailers. The trailers are utilized to transport ammunition, rations, and fuel to the battle area. The divisional companies have included only light tanks and tankettes (called armored vehicles by the Japanese).
(b) Nondivisional.—The Japanese tank regiment, which is nondivisional, is made up of 52 light and 95 medium tanks, a total of 147. Each unit down to and including the company has, in the rear echelon, a service detachment which supplies ammunition, fuel, and limited maintenance. The rear echelons also probably include light armored and half-track maintenance and supply vehicles. Each medium tank carries four men, a commander, a machine-gunner, a cannon-gunner, and a driver. Organizational details of the tank regiment are shown in the diagram on page 26.
(3) Tactics.—The Japanese have employed small groups of tanks—from three to five—in direct frontal attacks to assist the forward advance of the infantry. The tanks have been with drawn when the infantry has reached its objective. All these tanks are a light type except the leader, which is a medium. In Malaya, sometimes these groups were composed in whole or in part of armored carrier vehicles with one medium tank used as the leading element. Clearing enemy troops and obstacles off roads and creating confusion among the defending troops were the usual missions these tank groups. The groups sometimes attacked in as many as four waves. The leading wave sought, without stopping, to engage vehicles and personnel on or near the road, while the rear groups halted on the road and opened fire when opposition was encountered. However, none of the groups pursued the attacks a great distance from the road. Their fire usually was inaccurate, and casualties were light. After brief engagements the groups would move by roads deeper into opposition territory and engage other troops in a similar manner, particularly directing their efforts at troops in the rear, at artillery, at command posts, and at supply installations.
| Figure 4. Organization of Japanese tank regiment. |
c. Bicycle Troops
(1) General.—Bicycle troops are organized separately from the infantry. To date Japan has employed only a comparatively small number of cyclist troops. Most of these were used in Malaya. Indications are that all bicycles utilized were confiscated from the natives and used only in movements behind the front lines.
(2) Organization.—The bicycle troops usually were observed in groups of 60 to 70.
(3) Movement.—No definite formation was kept in movement, but two or three were abreast and separated a few yards from the man in front. The cyclists traveled 8 to 10 miles an hour in daytime but appeared to be in more of a hurry at night. They also made more noise at night—as if they were somewhat nervous. About 1 in 10 carried a flashlight; about half of the flashlights were tied on the bicycles. The movement of bicycle troops was not coordinated with motor transport except possibly with motorcycles. The latter were seen going in the same direction as the bicycles in nearly every case but at speeds of about 30 miles an hour. No one stood out among the cyclists as a leader, either by dress, position, or behavior, and it is believed that their officers rode on motorcycle combinations. No scouts were observed and security precautions appeared lax.
(4) Equipment.—Each cyclist carried what appeared to be a rifle. The rifles—some of which were shaped as if they were automatic—usually were transported with the barrels forward below the horizontal bar of the bicycle frame. More than half of them were carried in khaki covers. No rifles were observed slung on the cyclists' backs and in no case was a rifle detached from a bicycle when the soldiers stopped for rest or to enter a house. No pistols, knives, submachine guns, or items resembling ammunition were observed. The average load on the bicycle, apart from the soldier, appeared to be 75 to 100 pounds. The load included packs, which invariably hung on either side of the rear carrier; a box or bag of some type on the carrier; a rolled, hoodless rain cape; and other equipment, including spare clothes.
d. Flying Columns
(1) General.—Fast, hard-hitting combat teams known as flying columns have been employed by the Japanese in China. They included tanks, armored cars, motorized infantry, cavalry, engineers, and signal and medical personnel.
(2) Purpose.—The flying columns were designed primarily to make quick, effective surprise attacks on opposition forces of varying size. They made infiltrations, reconnaissances, and flanking and turning movements; they disrupted communications; harassed large formations; acted as the advance guard for the main body; and assisted the main body in difficult situations.
(3) Composition.—Although the strength of the flying columns varied according to the tasks performed, they generally were composed as follows:
(a) 1 section of armored cars—1 lieutenant in command.25 enlisted men (approximately), including 1 sergeant as car commander and 1 corporal.4 light armored cars, each carrying 2 light machine, guns.4 trailers.1 motorcycle, with attached sidecar.
(b) 1 section of tanks (light or medium)
4—1 lieutenant in command.30 enlisted men (approximately).3 tanks.1 motorcycle, with attached sidecar.
(c) 1 squadron of cavalry (4 troops)—Officers (number unknown but believed to be 5).165 enlisted men, including 2 sergeant majors, 1 noncommissioned gas officer, 1 noncommissioned veterinary officer, 1 noncommissioned supply officer, 2 buglers, and 1 medical orderly.155 horses (approximately).4 light machine guns.
(d) 1 company of infantry (3 platoons, with 1 platoon or more of heavy machine guns attached)—5 officers.189 enlisted men.12 light machine guns.129 rifles.159 bayonets.18 short rifles.Grenade dischargers (number unknown).
(e) 1 car section—1 lieutenant in command.15 drivers.15 assistant drivers.2 light machine-gunners.1 mortar-gunner.1 ammunition carrier.15 cars.1 machine gun.1 mortar.
(f) 1 section of engineers, including 5 NCO's.
e. Pursuit
With aircraft lending effective aid, the Japanese have carried out vigorous pursuits of United Nations' forces. Reconnaissance planes located and photographed oil, food, and ammunition dumps and storage points hi order that pursuit troops could later locate and confiscate the supplies.
The Japanese have been helped greatly in this phase of warfare by utilizing captured guns and supplies. Officers and ordnance personnel, schooled in the mechanics of various opposition equipment, particularly artillery, have been able to repair and operate this equipment immediately. Although the drivers of United Nations' vehicles in most cases removed the distributors from motor vehicles before abandoning them, the Japanese often had usable spare distributors, obtained from similar disabled vehicles.
The Japanese, contrary to the usual tactics in the past, always displace usable captured armament and supplies to the front—not to the rear. For instance, captured field guns are trucked or towed forward with the pursuit until dumps of appropriate ammunition are reached, and then they are put into action. Instances have been related by field artillery officers where the Japanese used pieces from which the breech blocks had been removed. They undoubtedly found the blocks or used similar blocks taken from the same type of gun. Japanese infantrymen often discarded their own rifles in the pursuit, after using all their ammunition, and armed themselves with opposition rifles. The same was true in the case of machine guns.
Pursuit parties moved so fast in Malaya that at times they were able to cut both civilian and military communications and arrive in cities and towns before civil authorities knew of their proximity or had time to remove or destroy vital stores of supplies. Often Japanese tanks and trucks appeared at filling stations for fuel and water. These successes spared the Japanese considerable effort in obtaining supplies from the rear.
f. Antitank Defense
Little information has been received on antitank defense.
(1) Antitank rifles.—So far there has been no mention of the use of antitank rifles. In the few limited operations in which the Japanese have been forced to protect themselves against tanks, defended road blocks have been established.
(2) Antitank guns.—The use of a 80-caliber dual-purpose antitank gun has been reported.
g. Defensive
Although Japanese soldiers have been taught that retreats are "inglorious," their training regulations indicate defensive tactics similar to those used by the United Nations. Positions are occupied in considerable depth. They consist of a number of defensive areas, each capable of all-around defense. Dummy positions are interspersed.
h. Deceptive Measures
Perhaps in no other military campaign in history has so much deception been used as in the current Japanese campaign. Deceptive measures employed by the Japanese to date include the following:
(1) Taking advantage of the difficulty in distinguishing the Japanese from Malayans or resident Chinese by frequently dressing as civilians and hiding their guns until they could spring a surprise attack;
(2) Dressing in British and Dutch uniforms and steel helmets;
(3) Putting captured Indian soldiers as a screen between themselves and attacking Indian troops with orders to urge the Indian troops to hold their fire;
(4) Hiring civilians to drive private cars to bridges prepared for demolition so that the Japanese hidden in the car could shoot the covering party;
(5) Making noises imitating frontal fire to attract the opposition while lightly armed Japanese troops worked around the flanks;
(6) Employing intelligence personnel with advance guards to confuse British native troops by speaking out in Malay, Tamil, Hindustani, Gurkhali, English, or Dutch-depending on the circumstances;
(7) Exploding firecrackers in the rear of defending troops to give them the impression that they were being attacked heavily;
(8) Rapping bamboo sticks on hard objects to imitate machine-gun fire;
(9) Exposing soldiers in a swimming pool and at a nearby bar in Borneo to draw the fire of Dutch machine guns so that their positions could be determined;
(10) Calling out in Dutch for the whereabouts of the Dutch commander during a night attack and shooting the commander when he answered.
i. Fifth Column Activities
Japan laid the groundwork for Asiatic conquests with years of intense propaganda in China, Indochina, Thailand, British Malaya, Burma, India, the Netherlands East Indies, and other southwest Pacific islands in British, American, and Dutch possessions. Rivaling Germany's far-flung propaganda activities, Japan was estimated to have had over 200,000 paid and schooled professional agitators at work in the above-named areas prior to the Japanese attack on the United Nations.
Until September 1941, the propaganda had been aimed mostly along cultural, educational, and political lines. Since then propaganda has been accelerated to arouse the natives against their governments so as to obtain their support for forthcoming military operations.
When Japanese troops first entered Malaya, in order to win over local support, they distributed Singapore money (printed in Japan) among a large number of natives. The same device (guilders, printed in Japan) was used in Borneo and other islands of the Netherlands East Indies. In addition, natives were told that the homes of the British and Dutch were theirs, and they were invited to move in and take them over or else to loot them of furniture and other valuables that the Japanese themselves did not want.
Reports of various Japanese fifth column activities since the war started disclose the following methods:
(1) Use of red-clothed scarecrows and arms pointing to defenses.
(2) Indication of the direction of targets by trampling or cutting arrows in rice fields.
(3) Pointing of banana leaves, washings, or planks to indicate motor transport parks or command posts.
(4) Dressing of civilians in occupied territory as British and Indian soldiers and their calling out to the British not to shoot.
(5) Furnishing of local food supplies.
(6) Use of fishing boats and lights to aid in landing operations.
(7) Indication of airdromes with strips of cloth or paint and by flashing lights.
(8) Acting as expert guides for Japanese troops.
(9) Supplying of information gathered before the war by local Japanese residents.
(10) Rendering of assistance as native officials.
(11) Natives in Burma cloaked themselves as priests or monks for the specific purpose of doing fifth column work—this was accomplished easily because of the loose requirements necessary to join the priesthood order of poongees.5
(12) Procuring of bancas and other small boats for Japanese infiltration parties which slipped down the west coast of Malaya.
(13) Tampering with air-raid warning systems to render them unworkable.
(14) Spreading of rumors among native troops.
(15) Maintaining a radio transmitter in Singapore through out the Malayan campaign.
(16) Drawing up of airdrome plans to turn over to the Japanese—a Malay overseer at Alor Star airdrome, Malaya, was arrested with airdrome plans, signaling apparatus, and Japanese propaganda.
(17) Two coolies walking together, one wearing a red shirt and the other a white, indicated the proximity of opposing troops.
(18) Drink vendors on bicycles signaled to the Japanese with a flag, waving it twice and pointing to British troops after they had served the British free drinks.
(19) A German dressed in civilian clothes preceded Japanese patrols by 50 yards and engaged opposing troops in conversation while the patrols took up firing positions.
(20) Telephone operators acting as chief fifth columnists in the Kedah, Malaya, area.
(21) Use of rice, salt, and white paper on roads to denote proximity of troops.
(22) Aiding in the organization of the "Free Burmese Army."
(23) Members of Thakins antiforeign political party in Burma organized to resist the British by fifth column activities and to join the "Free Burmese Army."
(24) German missionaries in New Guinea turned out to be fifth columnists—they helped the Japanese through the jungles to contact Australian forces.
(25) Obtaining information direct from United Nations' airfields—possibly by transmissions from nearby undetectable short-wave radio sets6 to adjacent field transmitters and then to Japanese air headquarters.
(26) Dropping propaganda pamphlets from the air, and having Fifth Columnists distribute them even more widely during blackouts.
(27) Signalling to Japanese aviators by placing lights in hollow stumps where they could not be seen from the ground.
(28) Placing "puncture traps" on Burma roads to damage or delay United Nations' motor transports. The traps consisted of several sharp steel spikes, cut out of one-fourth-inch flat steel sheeting. The spikes were 6 inches long, with the upper 3 inches protruding from the road bed and camouflaged with mud, straw, or dried leaves.

Operational Task
One of the most common mistakes is to treat all armored vehicles as tanks. Armored cars, self-propelled guns, armored personnel carriers and several other types of armored fighting vehicles can be and frequently are misidentified as tanks, just as every warship is a "battleship" to most civilians. In real life all of these vehicle types and more are commonly lumped together under the catch-all term "Armored Fighting Vehicles" which is usually contracted to just "armor" or, if you want to be all snooty about it, AFV (no relation). Despite the common logic of "if it looks like a tank, acts like a tank, smells like a tank, it's a tank", many AFVs that look like tanks don't fit the definition, as tanks are usually characterized by being more of a product of old warfare, therefore way more heavily armoured and generally built to take the brunt of enemy fire than their AFV cousins, which usually possess lighter armour and rely more on indirect combat. Of course, this makes tanks rather expensive to make and maintain compared to other armoured vehicles, which is why we're seeing fewer actual tanks portrayed by the media these days.
In most war films, particularly those set in the Second World War, historical tanks and armored vehicles will be replaced by either modern or more widely available contemporary vehicles that have either been painted in appropriate (or at least stereotypical) color schemes or given cosmetic makeovers to disguise their foreign or anachronistic features. The amount of effort that goes into this varies rather wildly.
There are many very good reasons for this. Firstly, antique armored vehicles are actually quite scarce. Some vehicles — particularly those from the defeated Axis nations — were never exactly common in the first place. Fewer than 500 King Tiger tanks were produced as opposed to 47,000 M4 Shermans, and many contemporary Italian or Japanese vehicles were produced in even smaller numbers, surviving examples simply may not even exist (Unless being scattered in small pieces across remote Pacific islands or buried in the Russian steppe counts as "surviving"). To make it even harder, some of these vehicles are now historical artifacts belonging to museums and obviously cannot be used recklessly or destroyed.
Next, as the Sherman production numbers above suggest, filmmakers naturally took advantage of the huge glut of cheap surplus U.S. Army equipment in the immediate postwar period. If a studio has running vehicles in their prop inventory that are available for filming without much hassle, then simple convenience means they'll get used, accurate or not. These days, most armored fighting vehicles that don't meet their end on the battlefield will probably be scrapped before anyone else can get their hands on them. Tanks have never been particularly attractive on the surplus market since they are huge, heavy, fuel-guzzling lumps of steel that can easily cost more to restore and preserve than recycle.
Even contemporary vehicles in operating condition can be prohibitively hard to find and incredibly expensive to hire, transport and maintain for filming. After all, tanks tend to be just so flipping big and in part because military vehicle collectors are often understandably leery of renting their rare and often irreplaceable treasures to people who are just itching to crash them, burn them, blow them up or drive them off cliffs.
Then there's the matter of Real Life politics, where vehicles you'd ideally want for realism simply can't be obtained at all since they're currently being used or held by an unfriendly power. It's easily forgotten today that prior to The Great Politics Mess-Up, getting realistic Soviet or Eastern Bloc military vehicles for filming many a Cold War thriller was darn near impossible. Whereas today, you can just phone the Russians and ask them nicely.
Similar to its sister tropes, this one happens out of practicality more than anything else, especially if you're not Backed by the Pentagon and just don't want reality to get in the way of Tank Goodness. Just find something vaguely tank-like, add a coat of stereotypical (but historically inaccurate) panzer gray paint and a few crosses and voila! instant Tiger. And—let's be honest here—aside from a few vehicle enthusiasts and history buffs, most viewers wouldn't even notice (or care), anyway. If it has tracks and a gun, it's a tank as far as they are concerned and it doesn't violate their Willing Suspension of Disbelief. To those who know what to look for, however, it can quite jarringly break it.
For producers who care, there are a number of ways around it. One is to use surplus or 'backup tanks' from modern armies such as Russia or Spain: Most T-34 and Sherman tanks used in WWII films were not actually from the war but modernized vehicles from the immediate postwar period. Another is to take a more common modern or contemporary vehicle and give it a cosmetic makeover to give it the appearance of the correct historic vehicle; sometimes these conversions can be quite sophisticated with only a few detail differences such as turret location and suspension design that only dedicated military vehicle enthusiasts would likely notice (these folk are often called "rivet counters" in the trade and are usually considered to be very annoying and hard-to-please people). Finally, there are always models of both the real and the Computer Generated variety, which naturally come with their own sorts of problems. Armored fighting vehicles are a relatively recent development of military capability. Superseding the horse cavalry during and after the First World War, new theories on armored warfare slowly displaced the age-old concepts of infantry and cavalry driving an offensive battle, until by the eve of the Second World War there were few major powers who had not seen the need for some kind of armored vehicles. The history of armored warfare, like any other technological advancements designed for the military, have suffered at the hands of politicians, languished on the books of economists, and been compromised by the higher echelons of command. Fortunately for the armor theorists, their ideas were eventually proven sound and the tank took its place as a major battlefield component, forging the way for maneuver warfare and the further development of combined arms theory.
WORLD WAR I
Although the tank first came into use during the First World War, the basic principles of armored warfare had been used for hundreds, even thousands, of years. The notion of a heavily armed and armored mobile force which could strike deep into enemy territory was first embodied by the heavy cavalry and chariot units of ancient times, as well as by the infantry tactic known as the “tortoise” which was used to assault fortified installations. However the need for a self-propelled armored vehicle was recognized much earlier in history.
The Spanish used horse-towed sleds with small cannons mounted on them to provide close artillery support for their troops in the field. The famous inventor and artist Leonardo de Vinci recognized the need for a heavily armored, but mobile, engine of war and drew up plans accordingly. In World War I, the need became apparent for a vehicle that could resist the machinegun, a weapon that had completely dominated the flesh and-blood battlefield of man and horse. At first, the use of simple armored cars was common; however, it was soon obvious that these vehicles, based on the limited suspensions of the period automobile and truck, were impractical on a battlefield which was covered with bomb craters, trenches, and barbed wire. A new solution was needed and, thanks to the invention of the caterpillar track, the tank was born.
The First Tanks
The British were the first to recognize the need for an armored vehicle capable of traversing the battlefield. Their first design, ordered by Winston Churchill (then First Lord of the Admiralty), called the No. 1 Lincoln machine, was built in 1915 and subsequently modified through the addition of superior tracks to become the Little Willie. This vehicle could easily cross a five-foot (1.52 m) trench and climb up a four-and-a-half foot (1.37 m) obstacle. For performance and armament, it had a top speed of 3.5 MPH (5.6 km/h), light armor, and fittings for a 40mm gun in a small turret. This early design was superseded by Big Willie, a now-familiar design utilizing the rhomboidal-shaped chassis and tread system with guns mounted on the hull sides instead of in a turret. The frontal armor was only 10mm thick, with a crew of eight men, a top speed of 4 MPH (6.4 km/h), two 57mm guns in hull sponsons, and four pivoting machineguns. This basic vehicle was tested in early 1916 and ordered into production in two versions; the “male” version, mounting the twin 57mm guns, and the “female” version which replaced the two cannons with two additional machineguns. Although they appeared earlier, mainly for local testing, the British Army’s first major use of tanks in combat took place on November 20, 1917, at the Battle of Cambrai, where the British used 400 tanks to penetrate almost ten kilometers into German lines.
The German Army then started to put their own tank into development - the A7V, which had a maximum of 30mm of armor, a 57mm gun in the hull front, six machineguns, and a crew of 18 men! The A7V was unwieldy, with generally poor performance, and a requirement for an enormous crew of soldiers from several different branches of service. As a result, less than 35 were actually produced. The French, also seeing the need for such a vehicle early in the war, had produced several heavy tank designs and one exceptional light tank design, the Renault FT-17. This tank, along with the British Mk.VI, a late-war version of the Big Willie, was adopted by the US Expeditionary Forces, which did not come up with an indigenous design until after the war ended in 1918. The FT-17 was the first “modern-style” tank design, mounted with a 37mm gun in a small, one-man turret, with the hull suspended between low tracks, and the engine situated in a rear compartment. The crew consisted of a much overworked commander/gunner/loader and a driver. Italy produced an improved version of this vehicle known as the Fiat Tipo 3000 Modello 1921, which also did not enter service until after the war.
The First Tankers
Nearly every major nation had its own outspoken supporter of the tank during this critical period of armor development. Colonel Ernest Swinton was the most outspoken advocate of armored warfare in Great Britain, and was heavily supported by future Prime Minister Winston Churchill, as well as Major J. F. C. Fuller, who later invented and refined many of the early tactics and techniques of armored warfare. It was largely due to Swinton’s efforts that the British tank design program was initiated in 1915. General Elles, the commander of the successful British armored attack at Cambrai, was also one of the early pioneers. Lieutenant Colonel George S. Patton, Jr., who was later to become famous as commander of the Third Armored Division in World War II, was also an early supporter, and one of the first American tank officers to fight (in September, 1918). The first American armored warfare school, located in Pennsylvania, was established by another officer whose experiences would heavily influence the outcome of WWII: Captain Dwight D. Eisenhower. Among the French, it was Colonel Jean Baptiste Estienne who managed to convince his commander, General Joffre, of the need for armored fighting vehicles. It was also he who envisioned the first successful light tank, the aforementioned Renault FT-17, and obtained the authority to have them designed and built. It was not until after the war had ended and the effectiveness of the tank in action proven, that Germany and the Soviet Union, the two major proponents and innovators in armored warfare from then until the Second World War, took a more serious interest.
More to come as tanks and tactics continue to develop between the World Wars... http://www.cbc.ca/archives/ http://www.cbc.ca/news/technology